5 Considerations for Your Third-Party Risk Management Program
/GUEST BLOGGER
John Thackeray
Founder and CEO of Risk Smart Inc.
Fraud risk management should both inform and shape any third-party risk management program in conjunction with all the other risk disciplines. Now more than ever, with increased regulation and risk, organizations must conduct vigorous, structured and regular due diligence on third-party intermediaries. The risks posed by these parties are many and varied, ranging from cybersecurity to business disaster. With third parties accessing regulated company information, the likelihood and impact of IT security incidents are on the rise.
Regulators are looking for the methodology, the approach and the sustainability of programs designed to capture and mitigate these risks. Moreover, regulators are seeking evidence on how a program and its processes are embedded and aligned within an organization’s risk culture and risk appetite.
Possessing a robust, structured program to mitigate these risks can protect corporate reputation and shield executives, board members and other management from personal and professional liability. At its core, such a program incorporates a risk-based approach, which is a methodical and systematic process of knowing the company’s business, identifying its risks and implementing measures that mitigate those risks.
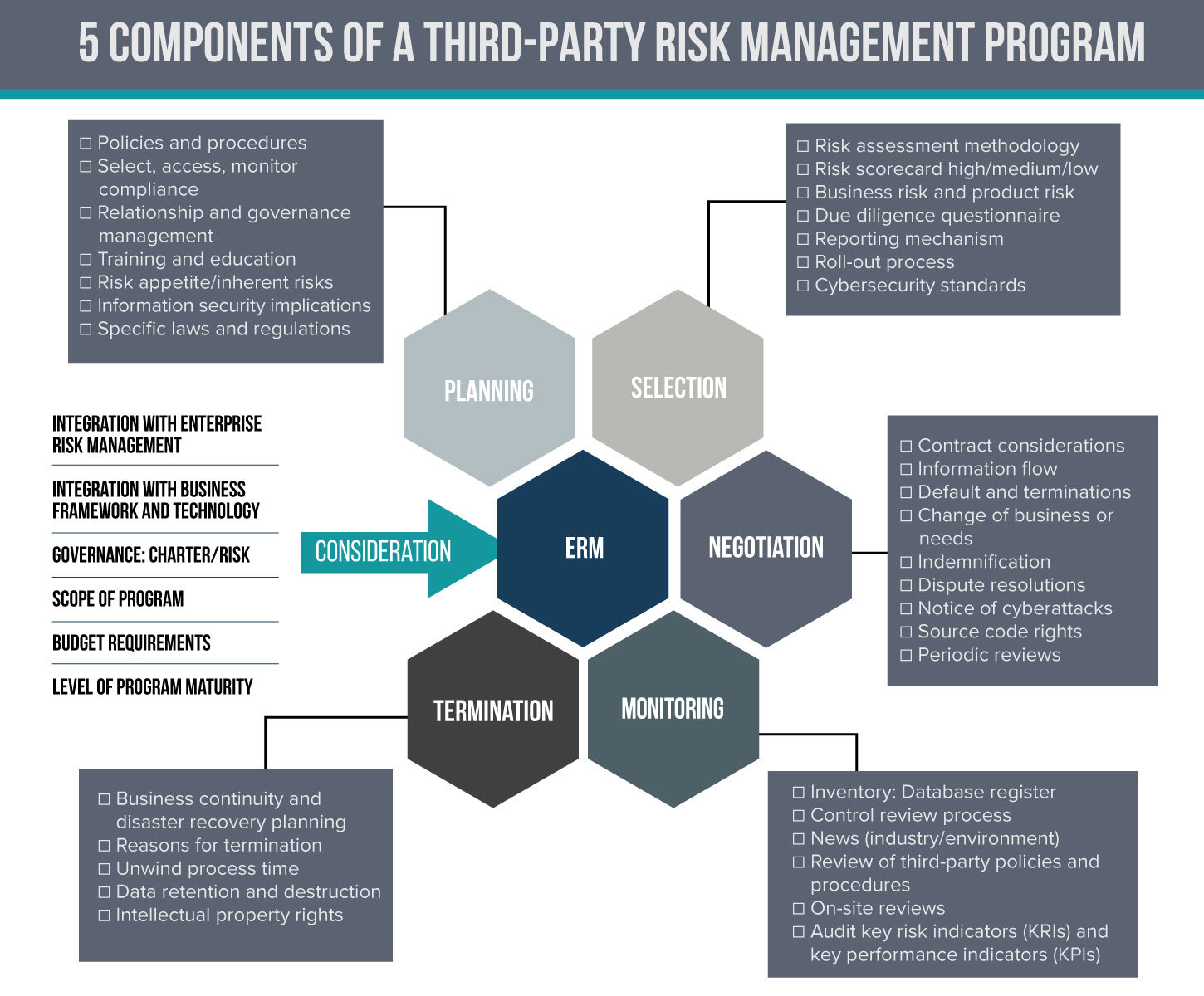
The diagram below portrays the key considerations which are explained further below.
Planning
Each third-party relationship brings with it several multidimensional risks that extend and traverse across suppliers, vendors, contractors, service providers and other parties. An effective third-party risk management process begins by comprehensively identifying third-party risks. This risk identification process should be followed by an analysis of the specific drivers that increase third-party risk. Moreover, your organization needs to understand its universe of vendors and how the third-party ecosystem engages, interacts and connects with its internal and external operating environment.
With an understanding of its risk appetite for vendor risk, a risk framework can be developed with a coherent and consistent set of policies and procedures which define the paradigm of an objective risk assessment model, crucial in creating a risk profile for third parties. The policies and procedures will, furthermore, describe the implementation of the system, resources, acceptable mitigants, roles and responsibilities.
Selection
Your organization should take a risk-based approach to third-party screening and due diligence. Stratify your third parties into various risk categories based on the product or service, as well as the third-party’s location, countries of operation and key contributions. An important part of the process will be to mitigate an over-reliance on any key third party.
Negotiation
Standardized contracts are a must, outlining the rights and responsibilities of all parties, with suitable metrics in place to sustain the relationship. Given the importance of supply chains today, the contract should identify any subcontracting to a fourth party. The key is to contractually bind third parties to inform and get approvals on any fourth-party involvement and ensure that fourth parties are in the scope of screening and risk management processes. Understanding the business continuity process and the compliance requirements of the third party are also important considerations in the selection process.
Monitoring
Monitoring is essential as it will ensure that performance standards set by the program are being implemented and followed with the imposition of well-defined metrics to measure the effectiveness of the program. Continuous third-party monitoring and screening is the key to helping companies make informed decisions about their third parties, with screening against global sanctions lists, law enforcement, watchlists and adverse media reports.
Termination
The termination process is often overlooked, but it’s so crucial in the negotiation. It should take what-if scenarios into account, with various trigger points that allow your organization to extricate itself from the relationship in an orderly and timely fashion.
Third-party risk management is one of the top emerging risks, and fraud risk management needs a seat at the risk table to both impact and inform the program but more importantly keep it relevant with regard to outside influences. Fraud risk management can no longer be a silent partner when it comes to third-party risk management.
John Thackeray is the founder and CEO of Risk Smart Inc., a consulting firm that specializes in the writing of risk documentation. Over his long career, he has held many risk positions, including CRO posts at Societe General and Penson Worldwide Holdings, where he interacted and engaged with U.S. and European regulators.